Flowmon Anomaly Detection System is at the forefront of the technology-driven battle against modern cyber threats that bypass traditional perimeter and endpoint security. Whenever new security or operational issues arise, Flowmon ADS is the light providing IT professionals with detailed network visibility and powerful behaviour analytics to take decisive actions and manage the network with confidence.
Key features and benefits
- Automation
- Threats are detected instantly and automatically.
- Early threat alerting
- Behaviour pattern recognition detects threats in their infancy.
- Noiseless insight
- Machine learning and other sophisticated algorithms combined to deliver accurate insights.
- Low rate of false positives
- Behaviour patterns, reputation feeds, and IoCs to complement NBA.
- NetOps and SecOps together
- Flowmon ADS is a common grounds for collaboration on incident resolution.
- Short incident response time
- Context-rich incident visualisation for instant remediation.
- Low and slow stage detection
- Attacks are detected before traffic spikes, preventing danger from escalating.
- SecOps ecosystem integration
- The solution is integrable with event logging, ticketing and incident response systems.
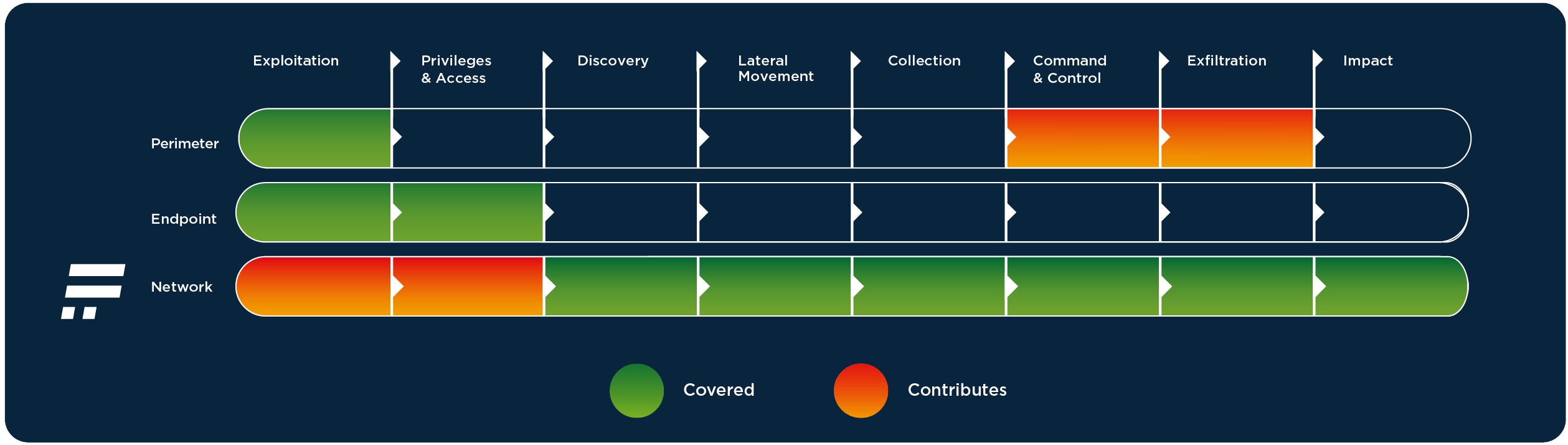
Advantage at every stage of compromise
Traditional signature and rule-based detection approach like firewall, IDS/IPS or antivirus focus on securing perimeter and endpoints. Effective though they are in detecting initial infection by known malicious code or behaviour, they offer no protection beyond perimeter and endpoint - a vast area where insider threats occur. Exploiting this gap is the most common way of stealing data. Insider threats can only be uncovered by detecting the slightest anomalies that show indicators of compromise.
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Dortmund is ready to assist you.